
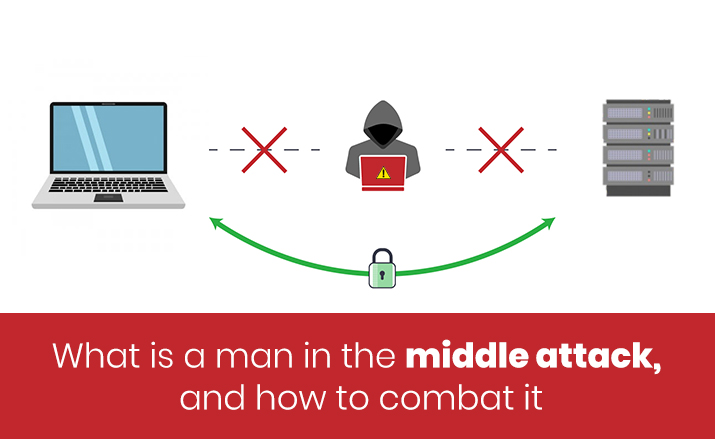
A man in the middle attack (MITM) is a hijack by an attacker who secretly intercepts the direct communication between two people either by relaying or altering their connection with certain hi-tech tools and techniques. There are three parties involved in this process, the attacker and the two victims. Many examples of MITM attacks are prevalent not just online but also offline. Eavesdropping is a part of the MITM attack wherein the attacker creates a connection to the victims independently while relaying them the message. In this, the victims think that they are communicating with each other securely but it's the attacker that controls their chats and alters it as per the need.
Some of the most prominent MITM attacks happen with the use of certain online methods by the attackers. It includes spoofing of HTTPS, DNS, and IP address of the users to compromise their online identity. Also the Wi-Fi eavesdropping, SSL and email hijacking, stealing browser cookies do lead to the attackers getting the personal data of a user comprehensively.
There is a term called a man in the browser attack in which the attackers use the phishing technique to send an email, or text message containing a link from a trusted source generally for a service purpose. Once the victim clicks on it, then the virus or malware gets installed in their digital device only to transfer the data related to logins and finances to the attacker. With that, MITM is a real menace for the users who are using the digital device to conduct their daily tasks. Hence, it is essential that you must install the secure PC cleaner software from the IGS Cleaner to combat the attacking threat of any kind on your PC. With the use of this software, you can efficiently protect your PC as it has a great set of features that scans, detects, and removes the viruses and malware from the PC completely.
So it can be said that the man in the middle attack (MITM) can be thwarted off quite successfully if you are careful in terms of using digital devices like PCs efficiently. Using the best PC optimizer software is a primary requirement to take care of your device from the potential MITM attack. As the attackers are always on the lookout for vulnerable PCs to do MITM attacks, you need to be ready for any possible threatening situation on your with this multi-featured security software. In all, you must stay informed and updated at all times while having the best security and protection for your PC.